Ransomware is an insidious new form of malware that is fast becoming the tool of choice for criminal hackers. Ransomware is dangerous, is increasingly sophisticated, and is becoming ever more common.
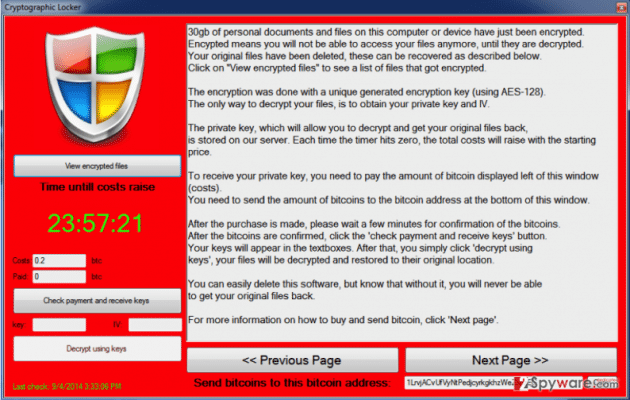
- Lock-screen (or non-encrypting) ransomware - prevents you from accessing your computer. When you turn your computer on you are presented with a lock screen demanding payment. Many variants of ransomware claim to be an “official” demand for a fine
- Bogus anti-virus (scareware) ransomware – claims to detect bogus problems (such as viruses) on your computer, and demands payment to “fix” them. This form of attack will often let you continue to use your computer, but will plague you with alerts and pop-ups, while also preventing you from accessing some programs. The good news is that this form of ransomware is usually the easiest to get rid of.
Thanks to the high likelihood of an easy payoff, cyber-criminals have taken to ransomware like fish to water. In June 2013 McAfee observed that the incidence of ransomware had doubled over the last year, after discovering 250,000 unique samples. In 2015 the FBI says it received 2,453 complaints about ransomware hold-ups, costing victims more than $24 million dollars. Notable examples of ransomware include Cryptolocker (now isolated), CryptoLocker.F (unrelated to CryptoLocker), CryptoWall (a clone of CryptoLocker), KeRanger, RSA4096, Manamecrypt, and Reveton.
Ransoms vary from between $10 to many hundreds of dollars and are usually demanded in Bitcoins.
Ransomware originally primarily targeted Windows PC’s, but versions that target all major platforms (including mobile ones such as iOS and Android) are increasingly common.
How does ransomware spread?
The primary vectors for the spread of ransomware are:
-
Phishing attacks – bogus or misleading emails that attempt to lure you to a website that is tricked-up with malware, or to download a malicious attachment.
-
Malvertising – which injects malicious or malware-laden advertisements into legitimate online advertising networks and webpages. A good example of this is the malvertising attack that recently hit the New York Times and BBC.
-
Other Infected computers – once files are infected, ransomware is easily transmitted between them via LAN networks or email, etc.
-
Pirate “cracks” – on torrent sites (and similar) it is common for program “cracks” or keygens (such as those used to pirate Adobe products) to be infected with ransomware.
How do I protect myself?
-
Backup, backup, backup
Regularly backing up your data is always a damn good idea, anyway, but is defiantly the very best defense against ransomware attacks. I always recommend implementing the 3-2-1 backup system (the original file, a second “local” copy, and a third copy stored on a cloud service.)
Be sure to keep your local backup files separate from those on your computer. Do not store them on a local hard drive - you should use an external hard drive which you disconnect once backup is complete. This will help to ensure that your backup files do not become infected if those on your computer do.
You should also backup regularly.
-
Just say no!
Receive an email that looks dodgy, or is from a sender you don’t know or are unsure about? Do not open it, let alone follow any links it contains, or download attachments!
The same goes for clicking online ads, and anything else that you are unsure about.
-
Use an adblocker
These can protect you against some forms of malvertising, although I personally recommend using Privacy Badger + uBlock Origin instead. These browser extensions are not specifically adblockers, but will block most ads and are highly effective at preventing advertisers from tracking you across the internet.
NoScript is another good option for Firefox users. It is a real pain to use, but provides the highest level of protection against malicious scripts on websites available.
-
Use anti-virus software and keep it patched
Anti-virus and other security software (such as phishing detectors) can be very effective at identifying and blocking ransomware attacks. No security product, however, can be considered 100 percent reliable.
This is particularly true due to the fact that new malware is continually being developed and released into the wild. This is why it is vital to keep your virus software definitions up to date, and all your security related software (which includes the Operating System itself) patched with the latest security updates.
Help! I’m being held to ransom!!!!
So the worst has come to the worst. Your files or your computer are being held to ransom by ransomware, and you do not have any backups of your key files (tut-tut). With ransomware the motto that prevention is better than a cure has never been truer, but it’s not time to panic (yet!).
Should I just pay?
In an ideal world, victims could stifle this proliferation of ransomware simply by refusing to pay money to the cyber-criminals responsible. When faced with losing valuable and irreplaceable data, though, it is easy to see why many cave in. I strongly recommend against paying, however, because:
- It only encourages the extortionists to commit more crime.
- There is no guarantee that the crook will not simply keep on demanding more money. After all, these are not honourable people!
So what should I do?
- Disconnect your computer from the internet - this will prevent your computer from infecting others, and in some cases may help to minimise how many of your files become infected.
- Check to see how many files are affected – then backup all those which aren’t. You should store these files somewhere safe, but where they cannot infect another computer (just in case). An offline external hard disk is ideal for this.
- Check them with an antivirus program - when opening these files on another computer. It is also a good precaution to then only open them within a sandbox (such as that provided by Sandboxie) or inside a Virtual Machine (such as VirtualBox). This will contain any malware infection they may still be carrying.
- Research the ransomware – security researchers are actively developing tools to combat ransomware and decrypt files or unlock lock screens. If you can identify the type of ransomware that has infected your machine, then tools may be available may be able to help you.
- Consult a computer technician or repair shop – in the case of more unsophisticated attacks, these may be able to help. They usually work on a no-fix no-pay basis, so you have little to lose.
- Panic!
Whatever the final result, it is a very good idea to completely reformat all your hard drives and reinstall your OS (or hard factory reset your mobile device).
Ransomeware Conclusion
Ransomware is fast becoming a scourge of the modern world, and is even more worrying when you consider that not just unlucky individuals, but large business and even governments are potential targets. As discussed, there are a number of things you can do to reduce the chance of becoming a victim yourself. But by far the best thing you can do is to backup everything that is important to you both religiously and regularly. For great reviews of various online backup services, you might want to checkout our sister-site, BestBackups.com!
