Zoom is a video conferencing app that has increased massively in popularity during self isolation. Because of that rise in popularity, Zoom is coming under much closer scrutiny - leading to more reports of insecurities, privacy concerns, and even the potential for hacking incidents caused by Zoom.
In this article, we will look at the privacy and security concerns surrounding Zoom. We also explain, in an easy-to-understand manner, what Zoom has actually done to ensure you are kept secure when using its platform.
Is Zoom secure?
Zoom is in constant development. Its application is regularly updated with security patches and updates each month. This is good, and shows that the firm is actively attempting to single out and deal with security vulnerabilities on its platform.
In a recently published report by Mozilla, Zoom was found to actually meet the firm’s minimum standards for security, giving the videoconferencing app a clean bill of health in five categories:
- Transport layer security encryption.
- Security updates.
- Vulnerability management (it has a bounty program).
- Password security.
- Privacy policy (Zoom claims not to use any data collected from users for advertising purposes).
Despite Zoom’s constant efforts to find and patch flaws, new vulnerabilities are still being discovered fairly regularly.
The firm has also admitted that it has had some teething problems going from being a platform primarily used by businesses with good security practices to a consumer-facing platform for individual internet users. However, it seems to improve all the time, which is generally a great sign.
So, what does this all mean? Unless you are using Zoom to discuss state secrets, matters of national security, company or trade secrets such as Intellectual Property, or sensitive personal and medical patient information - Zoom should be safe to use.
If you are still worried about zoom's security issues, then check out our best video conferencing apps page for a list of great alternatives.
Has Zoom been hacked?
Zoom has been a target for hackers in recent months. Below is a list of some previously discovered security concerns that have affected Zoom. Most of these issues have since been patched. However, it is believed that some zero-days remain viable. Therefore, it is theoretically possible that Zoom could still cause people to be hacked:
- Researchers discovered an exploit in which an attacker could remove attendees from meetings, spoof messages from other users and hijack shared screens.
- A security researcher discovered that Zoom’s anti-tampering mechanisms are not as competent as they should be, giving hackers the ability to potentially create infected versions of the app.
- Security researchers at Trend Micro discovered a version of the Zoom installer circulating that contained malware designed to mine cryptocurrencies.
- A security researcher previously revealed that recordings of Zoom meetings could be found online by anybody. According to the researcher, the URL structure for the recordings was predictable and easy to find, putting those recordings at risk. The flaw has since been mitigated with password protection for recordings. However, they remain discoverable.
- Reports previously emerged that hackers were selling two zero-day exploits for Zoom on the dark web. According to sources, the exploit would allow hackers to use Zoom to gain full control over a victim’s Windows computer. (Potentially still viable.)
- Security researchers from IngSights uncovered a set of 2,300 Zoom login credentials being shared in an online hacking forum. Researchers do not believe the data came from a Zoom breach, but due to credential stuffing attacks.
- A Zoom phishing scam circulated in which employees appeared to be asked to join a Zoom meeting by their boss. The link in the email forwarded the user to a fake Zoom login portal that phished them of their credentials.
- Zoom accidentally leaked the email addresses of thousands of users after accidentally listing them as being part of the same company. According to reports, how Zoom treated those users’ personal email addresses allowed them to start video calls with one another.
- Zoom was found to be passing data about Zoom users to Facebook, even when those users did not have a Zoom account.
Is Zoom safe for Mac users?
In the summer of 2019, it was revealed that Zoom had installed a hidden web server on Mac computers - forcing Apple to step in and secure millions of macOS devices with a security update.
According to the researcher who discovered the vulnerability, the web server could have been leveraged by malicious websites to activate the Mac’s webcam without the user’s permission. That vulnerability has since been fixed by Apple.
Security researchers also previously discovered Zoom exploits for macOS that allowed hackers to inject malicious code into Zoom’s installer (concerning because Zoom was also found to self-install without requiring consent from macOS users). In addition, a separate exploit was found that would let hackers hijack a victim's device to potentially take control of the webcam and microphone.
The good news is that those flaws have now all been patched. In addition, Zoom has updated its macOS installer so it no longer behaves like malware. So are macOS Zoom users safe?
There is always a potential that new vulnerabilities might be discovered in the future. As a result, the answer to this question will largely depend on your personal threat model. With that said, you should be ok to use Zoom for non-sensitive video conferencing.
On the other hand, some security researchers still find Zoom to be concerning and have warned against using the software. So if you really care about privacy and security, it is essential only to use Zoom alongside a top antivirus program, a strong firewall, and even a VPN for added encryption.
What else is Zoom doing to ensure it's secure?
Zoom has promised to devote all its time to ensuring any newly discovered vulnerabilities are patched before any further development of additional features is undertaken. This is welcome news, and for the most part Zoom appears to be a firm that works hard to patch up vulnerabilities as quickly as possible.
However, some security researchers have raised concerns over Zoom’s use of the bounty program to silence researchers. At least one security researcher refused to sign Zoom’s nondisclosure agreement (which meant they were ineligible for their reward) in order to be able to disclose details of the security vulnerability to the press.
It is also worth mentioning that in 2018, employees at Dropbox became so concerned with Zoom-associated vulnerabilities that they started their own bounty bug reward program that encouraged researchers to come forward with any Zoom vulnerabilities discovered.
Can Zoom still be hacked?
The list of security vulnerabilities that have affected Zoom is pretty long. This is concerning and may be enough to put some people off the platform.
Although Zoom is working hard to patch exploits as soon as they become known, it is unclear how many known zero-days are currently being exploited in the wild by cybercriminals. And it is always possible that new zero-day exploits could be discovered by cybercriminals, meaning that Zoom could still be hacked at some point in the future.
What is Zoombombing and how to avoid it
Zoombombing is the act of gate crashing someone’s Zoom meeting. Zoombombing can result in data theft and snooping, inappropriate content being shared, dangerous links being posted by hackers, and even hate crimes.
Most incidents of Zoomboming occur due to unsafe user habits. Specifically, the public sharing of the URL for a meeting. When people share a Zoom meeting URL openly online, the URL may be disseminated to unwanted people and this can lead to Zoombombing incidents.
The best way to avoid Zoombombing is to always share the URL for a meeting privately. In addition, all people invited to a Zoom meeting should be made aware that it is not OK to share the URL publicly. This should ensure that the meeting is protected against unwanted intruders.
Secure your session by:
- Putting a password on your meeting.
- Sharing the URL privately.
- Checking the participants before beginning your meeting, kicking anyone that doesn't belong.
Unfortunately, security researchers have proven that it is possible for cybercriminals to use computer software to cycle through potential Zoom meeting URLs rapidly. By doing so, Zoombombers may actually stumble upon your meeting ID to gatecrash a conference. For this reason, it is always a good idea to check all the members of a meeting before engaging in any conversations.
Fortunately, Zoom has now added security features to its service that allows the host of a meeting to kick out any unwanted meeting attendees. As a result, if someone causes trouble in a meeting or joins without an invitation, the host can boot that user.
Does Zoom implement end-to-end encryption?
Despite previous claims made by the platform, Zoom does not provide end-to-end-encryption (e2ee) for video conferencing calls. The encryption that Zoom provides ensures that all video data is secure in transit thanks to its use of TLS (the same encryption that secures HTTPS website).
This encryption stops eavesdroppers from being able to intercept your video and audio data in transit. However, user data must still pass through Zoom’s servers and because that data is not secured with e2ee it is possible that those conversations could be accessed, stored, or potentially analyzed by the company and any third parties it works with (as well as government authorities if it is served a warrant).
This fact has raised some concerns because it was discovered that Zoom routed some video calls via servers in China by default. China is a country where the government has an immense amount of power over businesses, and many people feel that any data held on Chinese servers can too easily be harvested by the Chinese government.
This has led the UK government to ban Zoom for official state business over fears of surveillance. The UK’s National Cyber Security Centre has stated that Zoom should only be used for public business.
Zoom’s CEO, Eric Yuan, has claimed that those conversations were only routed to China by accident, and a blog post released at the beginning of April claims that Zoom has taken steps to ensure that this no longer happens. Whether you trust the company to stop routing calls via servers in China is up to you. It is hard to verify those claims one way or another because Zoom is a closed source platform.
At the end of the day, unless you are using Zoom to discuss matters that affect national security, or other highly sensitive matters, you should be OK to use Zoom.
Update 04/06/20: Complaints over the discrepancy of Zoom's end-to-end encryption claims has led the firm to change its stance, with end-to-end encryption promised for paying members. Free members will not be included in this, however, having to make do with standard server-side encryption.
[[post-object type="blockquote" author="Eric Yuan, CEO of Zoom"]]Free users for sure we don’t want to give [end-to-end encryption] because we also want to work together with FBI, with local law enforcement in case some people use Zoom for a bad purpose.[[/post-object]]
Zoom CEO Eric Yuan has expressed that the intention is to work with law enforcement, but after privacy advocates including yours truly spoke out about the implications, the company has backpedaled to claim it only divulges information in extreme cases.
We do not share information with law enforcement except in circumstances like child sex abuse. We do not have backdoors where anyone can enter meetings without being visible to others. None of this will change.
Is Zoom bad for your privacy?
Besides the concerns raised above, it is worth mentioning that Zoom has some features that are concerning for user privacy. The attention tracking feature allows the host of a meeting to keep tabs on whether users are clicking away from the conference call. This has been denounced as an invasion of privacy that allows employers to track workers unfairly.
Zoom has also come under fire from privacy advocacy groups. Those organizations have pointed out that unlike companies like Google and Amazon, Zoom does not publish transparency reports regarding the number of data requests it receives from government agencies. Privacy advocates argue that this creates a shroud of secrecy regarding the level of surveillance occurring on the platform.
Zoom did recently update its privacy policy, however. Previously, the policy allowed Zoom to collect information about meetings - including videos, transcripts and shared notes. This data was believed to have been leveraged for marketing purposes.
Despite the improvements to its policy, which now clearly states that Zoom will not sell user data to third parties, Zoom does still collect data from users:
- IP address
- Phone number
- Operating System details
- Device level identifiers ("MAC address, other device ID (UDID), device type, operating system type and version, client version, type of camera, microphone or speakers, connection type, etc.”)
This is considered invasive by most privacy advocates, and the company admits that it will use location tracking to figure out your approximate location when you use its service.
Zoom also collects quite a lot of metadata regarding each call made. This includes information such as the user’s email address, name (or other information that a user enters to identify themselves), the name of the meeting, the date and time the meeting was scheduled, chat status, and call data records for Zoom Phone.
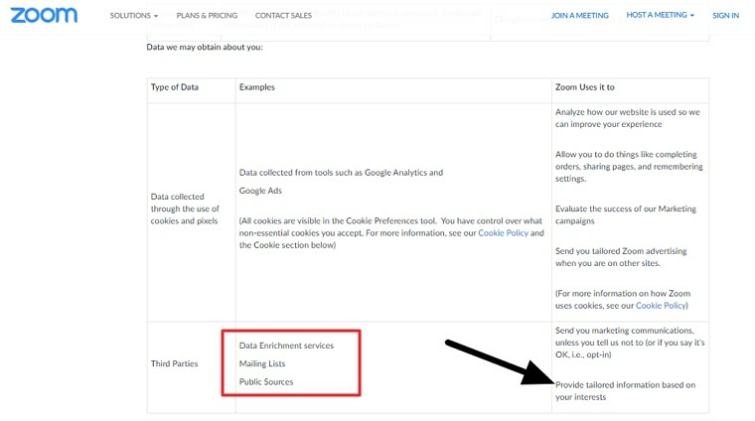
It is also worth noting that Zoom admits it will try to source more data about each user from "Data Enrichment services,” "Mailing Lists” and "Public Sources”. Thus, it seems fair to say that Zoom is actively engaging in attempts to create a database about its users with the intent to "provide tailored information based on your interests.”
This seems to fly in the face of claims made earlier in the policy that user data will not be used for the purposes of advertising.
Zoom alternatives
Generally speaking, most people should be ok using Zoom. However, if you feel unsure about the platform; stick to a secure open source alternative with strong end-to-end-encryption.
Here at ProPrivacy we have taken a close look at the best available options. To find out more about each option, please check out our best video conferencing apps guide. If you are in a rush, we generally recommend the following options:
- Jitsi Meet
- Wire
- Jami
- Nextcloud Talk
- BigBlueButton
Each of the options mentioned has both pros and cons, so be sure to visit our in-depth guide to find out everything you need to know about those services. And if you have any questions, don’t hesitate to drop us a message below!
